Enhancing Security with an Access Control Program
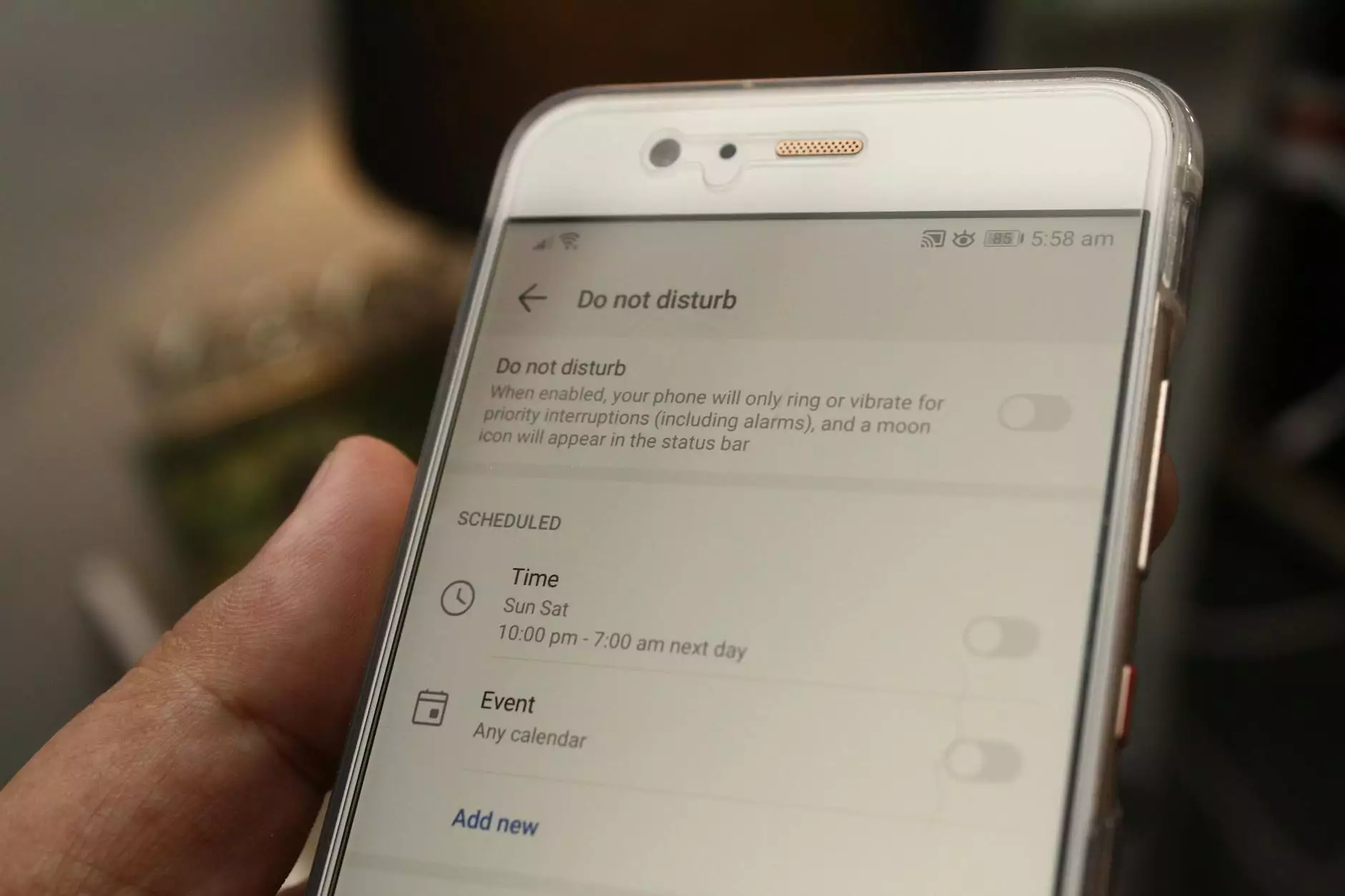
Introduction to Access Control Programs
The digital landscape is ever-evolving, and as businesses grow, so do their security needs. Implementing an access control program is essential for safeguarding sensitive information and ensuring operational integrity. Whether you are in the telecommunications sector, offering IT services, or providing computer repair, a robust access control strategy can significantly enhance your security posture.
Why Access Control is Critical for Businesses
Access control systems are designed to regulate who can view or use resources in a computing environment. Here's why they are vital for businesses:
- Protection of Sensitive Data: With the rise of cyber threats, protecting sensitive data such as customer information and financial records is more important than ever.
- Compliance with Regulations: Many industries are subject to strict regulations that require them to implement appropriate security measures.
- Improved Operational Efficiency: An access control program allows businesses to manage users effectively and streamline their operations.
- Prevention of Unauthorized Access: The primary goal of access control is to ensure that only authorized personnel have access to critical systems and data.
Components of an Effective Access Control Program
Creating an effective access control program involves several key components:
1. User Identification
Identification is the first step in the access control process. It ensures that each user is uniquely recognized. This can be achieved through various means:
- Username and Password: The most common method, but requires strong password policies.
- Biometric Systems: Fingerprints or retina scans provide high security.
- Smart Cards: Physical cards that grant access to authorized users.
2. Authentication Methods
After identification, authentication validates whether the user is who they claim to be. Methods include:
- Two-Factor Authentication (2FA): Adds a second verification step.
- Multi-Factor Authentication (MFA): Requires multiple forms of verification for increased security.
3. Access Control Policies
Implementing clear and comprehensive access control policies is crucial. Policies should define:
- User Roles: Specify what information and resources each role can access.
- Access Levels: Different levels of access should be granted based on necessity and roles.
4. Monitoring and Auditing
Continuous monitoring and auditing of the access control system are necessary for detecting breaches and ensuring compliance. Regular audits can help identify potential vulnerabilities and improve security protocols.
Implementing an Access Control Program in Telecommunications
In the telecommunications industry, safeguarding networks and customer information must be a priority. Implementing an access control program brings numerous benefits:
- Secure Network Infrastructure: Protects against unauthorized access to network resources.
- Customer Trust: Enhances reputation by demonstrating a commitment to data protection.
- Regulatory Compliance: Ensures adherence to telecommunication regulations and standards.
Maximizing IT Services and Computer Repair Security
IT service providers and computer repair businesses handle a multitude of sensitive customer data. Emphasizing an access control program helps in various ways:
- Data Protection: Protects customer data from breaches during repairs or service.
- Operational Integrity: Ensures that only authorized technicians can access critical systems.
- Risk Mitigation: Reduces the risks associated with data loss or theft.
Challenges in Access Control Implementation
While implementing an access control program is essential, challenges may arise:
- Resistance to Change: Employees may be resistant to new technologies and stricter access policies.
- Cost Implications: Initial implementation costs can be high, but the long-term security benefits outweigh this.
- Complexity: Designing a user-friendly access control system that meets security requirements can be difficult.
Best Practices for a Successful Access Control Program
To ensure the success of your access control program, consider the following best practices:
- Regular Training: Provide ongoing training for employees on access protocols and security awareness.
- Regular System Updates: Keep the access control software up-to-date to protect against vulnerabilities.
- Regular Audits: Conduct regular audits to review access rights and policies.
Conclusion
In conclusion, implementing an access control program is a crucial step for businesses in today's security landscape. By enhancing data protection, ensuring regulatory compliance, and boosting customer trust, organizations can not only protect their assets but also cultivate a more secure environment. Whether you are in the telecommunications, IT services, or computer repair sector, prioritizing an access control program is essential for long-term success.
Future Trends in Access Control Programs
As technology continues to advance, so do the methods of access control. Here are some trends to watch for:
- Artificial Intelligence: AI can analyze user behavior and detect anomalies for enhanced security.
- Cloud-Based Solutions: These solutions provide scalable access control options for businesses of all sizes.
- Integration with IoT: As devices become more interconnected, ensuring secure access to IoT devices will become a priority.
Ultimately, adapting to these trends and continually enhancing your access control program will ensure your business remains secure and operationally efficient in an increasingly digital world.









